Information Security vs. Cyber Security vs. Privacy
What are the Differences Between Information Security, Cyber Security and Privacy?
This discussion aims at clarifying the differences between Information Security, Cyber Security and Privacy. While they sometimes overlap, they are different. This will help you assign accountability and responsibility to the correct people and teams.
First, let's whiteboard this. Here is how I represent this in my head.
Information Security
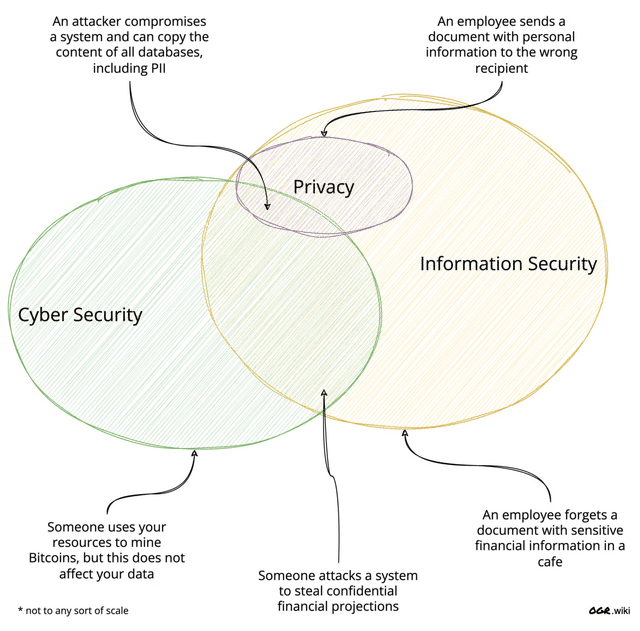
Information Security is about the protection of information from unauthorised access, use, disclosure, disruption, modification, or destruction. It encompasses protecting all forms of information, including electronic, physical, and verbal.
Privacy
Privacy is the right of individuals to control how their personal information is collected, used, and shared. It is a subset of information security, just for a particular category of information: Personally Identifiable Information (PII). It also happened to be tightly regulated in many countries.
Privacy is concerned with the individual's right to control their personal information. In contrast, information security is concerned with protecting all forms of information, including PII. While it overlaps, I treat Privacy as a subset of Information Security. From experience, this makes it easier when defining roles and responsibilities.
Cyber Security
Cyber Security is the practice of protecting systems, networks, and data from unauthorised access, use, disclosure, disruption, modification, or destruction. It is a related concept to information security, but it is different.
Roles and responsibilities
Your technology team can support some aspects of Information Security and privacy. But I’m ready to bet that it doesn't have the authority, budget, and organisational knowledge to influence business practices. Nor should it, to be fair. Technology should be an enabler, but it comes down to your business teams, which are essential to information security and privacy:
- A risky process when sending emails with potentially sensitive information?
- No consideration about data and privacy when using new fancy cloud services?
- Working around security controls without trying to work to understand or improve them?
The technology team also can’t know if Joe Blogg should have access to such and such business information. Only the information owner can make this decision. But it can help grant this access once they know, provided the information owner has delegated this responsibility to them.
Analogy
Let’s discuss an analogy between a car and information.
- Ownership
- A car is owned by its owner
- Information is owned by the Information Owner
- Regulations
- The car owner is accountable for ensuring they follow the regulations when driving
- The Information Owner is accountable for ensuring they follow the policies when using their information
- Right to use
- The car owner is accountable for ensuring their car meets the requirements (WOF, etc.)
- The Information Owner is accountable for ensuring the systems processing their information meet requirements (e.g., legal, regulatory or policies)
- Operations
- The car owner is accountable for day-to-day operations (e.g., filling the tank, cleaning the car)
- Can delegate responsibility to 3rd party (e.g., car valet service) but is still accountable to ensure it’s done well.
- The Information Owner is accountable for day-to-day operations (e.g., grant and review access and use the information appropriately)
- Can delegate responsibility to Technology/3rd party, but is still accountable to ensure it’s done well.
- The car owner is accountable for day-to-day operations (e.g., filling the tank, cleaning the car)
- Training
- The car owner is accountable for ensuring that the people they lend their car to are trained and follow good practices (e.g., train them or verify driver's licenses)
- But can delegate training to 3rd party (driving school)
- The Information Owner is accountable for ensuring that the people they allow access to or share information with are trained and follow good practices (e.g., train them or verify training certifications)
- But can delegate training to Technology/3rd party
- The car owner is accountable for ensuring that the people they lend their car to are trained and follow good practices (e.g., train them or verify driver's licenses)
- Maintenance of the system
- The car owner is accountable for delegating the tasks they can’t do to a mechanic, who ensures the car meet legal road requirement, change brake pads, top-up oil...
- The Information Owner is accountable for delegating the tasks they can’t do to Technology, who ensures the system processing the data meets the cyber security policies, patches servers, and secure services...
- Accreditation
- The car owner is accountable for ensuring that the car meets legal requirements and getting WOF issued for a time.
- The Information Owner is accountable for ensuring the system meets policy requirements and getting it accredited (typically by the CISO)
Technology can help, but it can’t solve everything. Ensure the right teams are made accountable and aware of their responsibilities.
Key Takeaway
- Your business teams are essential to information security and privacy.
- Your technology team is focusing on cyber security.
- Ensure the correct teams are made accountable and aware of their responsibilities.
Next steps
- Assess your risk. What are the top risks for your organisation? Which ones are related to information security? Privacy? Cyber security?
- Assign ownership. Are these risks assigned to the right people? Is it even clear to these people they are risk owners? Assign accountability to individuals and responsibility to teams to manage these risks.
- Get a plan and keep on top of it. Do you have a clear plan to manage these risks? Ask the owners (people you made accountable) to report on the plans and progress. Ask for evidence.